Abstract
Network-based tools have become a central component in the operation of many institutions such as businesses, universities and governments. The growing amount of sensitive data being transported over networks necessitates innovation to ensure these networks remain secure. Virtual Private Networks (VPNs) establish private connections between a remote user and a network. Since the rise in popularity of VPNs in the 1990s, many different VPN protocols have been created. Older VPN protocols that appear to be more theoretically sound often have a large amount of complexity, which increases their vulnerability. WireGuard is a newer, much simpler protocol with several user space implementations. Fuzzing, a technique for exposing vulnerabilities in software, may be a useful tool in exposing problems with user space implementations of WireGuard, thus enabling developers to make them more secure. In this study we investigate the viability of Peach and Boofuzz as tools for fuzzing network protocols, specifically Wireguard. We use both Peach and Boofuzz to fuzz "Wireguard-go", a user space implementation of the Wireguard protocol. We found that Wireguard-go demonstrated a reasonable level of robustness and in addition, was simple to run and configure. Furthermore, we found that the Peach fuzzer was not affected by differing switch count values. While the number of fields fuzzed, the maximum fields mutated per iteration, and the mutation strategies used did influence performance, the performance impact was minimal. Therefore, the impact of these parameters on performance is not sufficient to dictate decision-making when designing tests. A drastic decrease in performance was observed when the fuzzers were configured to restart the process on each iteration suggesting that restarting the process on each iteration should be reserved for only the most necessary cases.
Videos 1
Watch presentations, demos, and related content
In this video we motivate the need for our research and walk the viewer through our experimental process. We then present the results of our investigation and make recommendations accordingly.
Like, comment, and subscribe on YouTube to support the creator!
In this video we motivate the need for our research and walk the viewer through our experimental process. We then present the results of our investigation and make recommendations accordingly.
Gallery 8
Explore the visual story of this exhibit
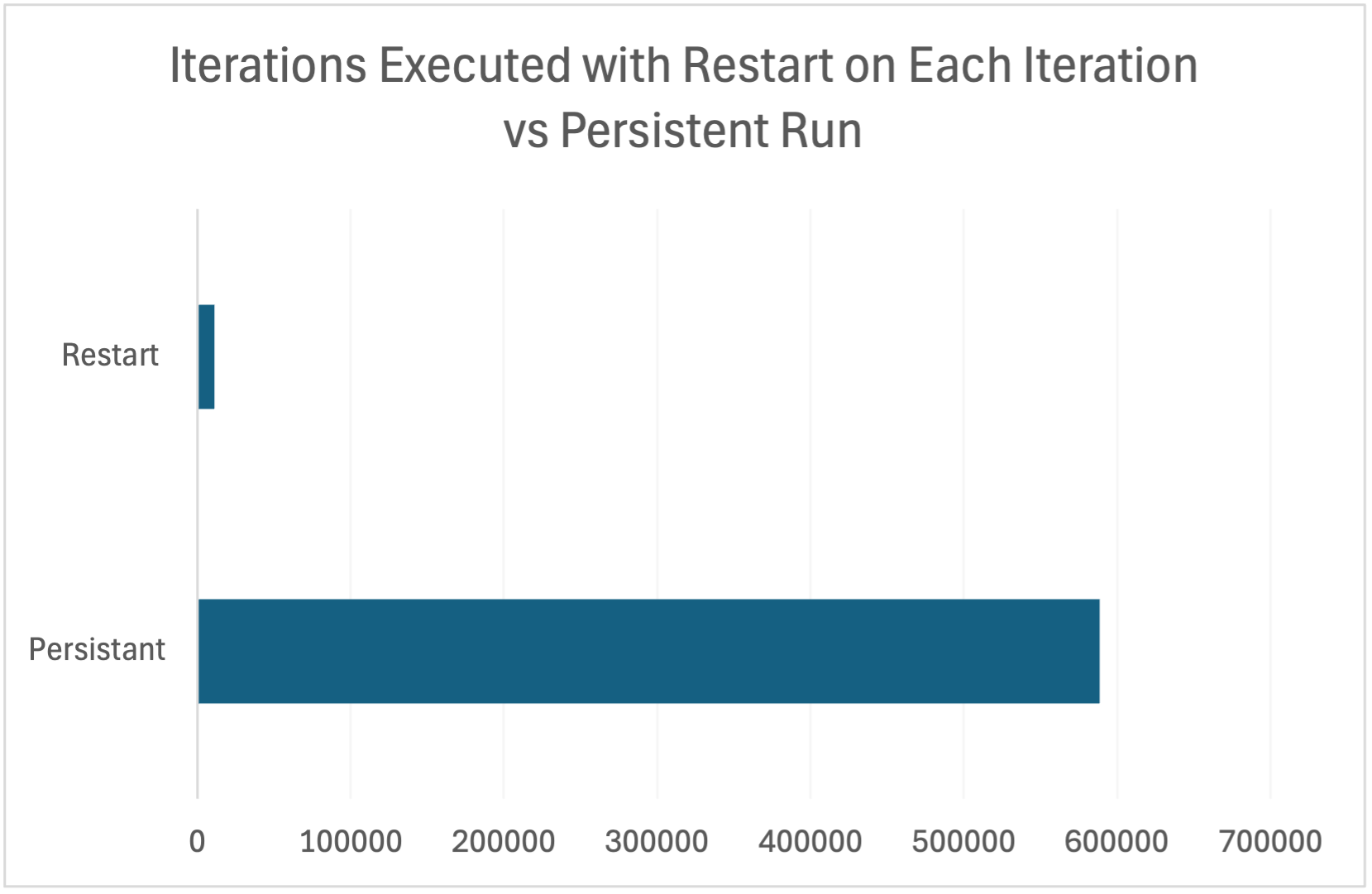
The performance of the Peach fuzzer when target process is run persistently vs restarted
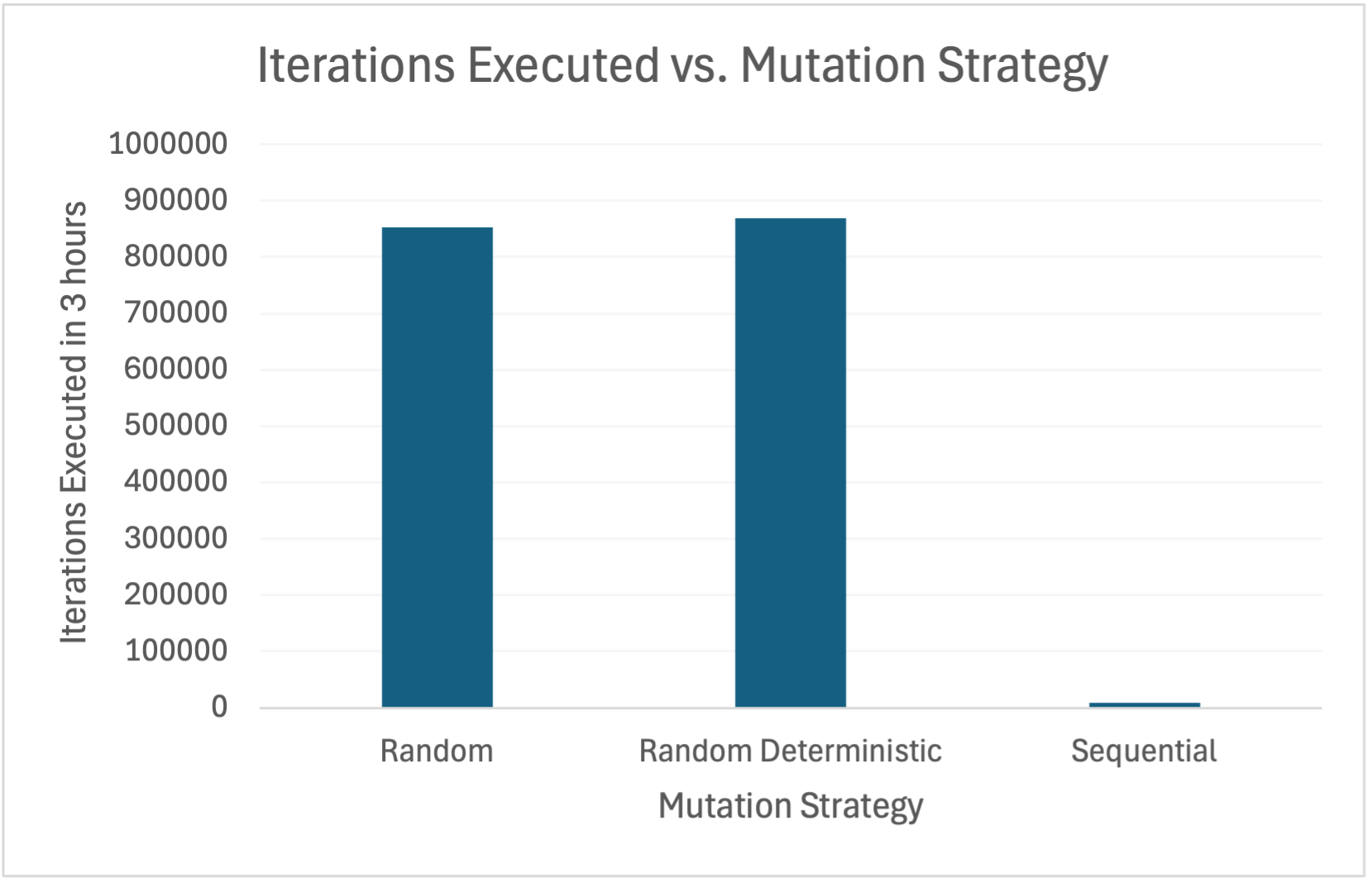
The performance of the Peach fuzzer for different mutation strategies
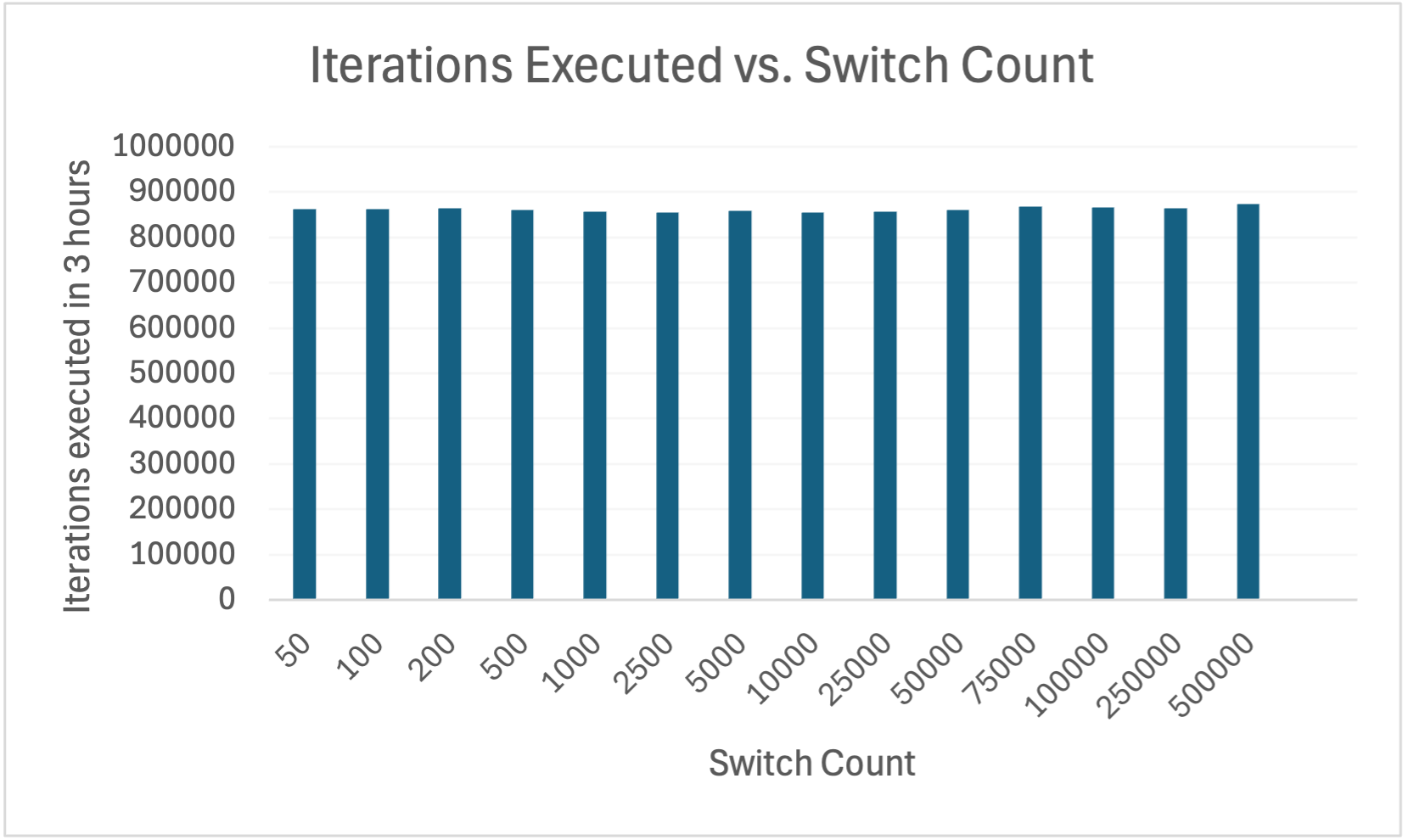
The performance of the Peach fuzzer for different values of switch count
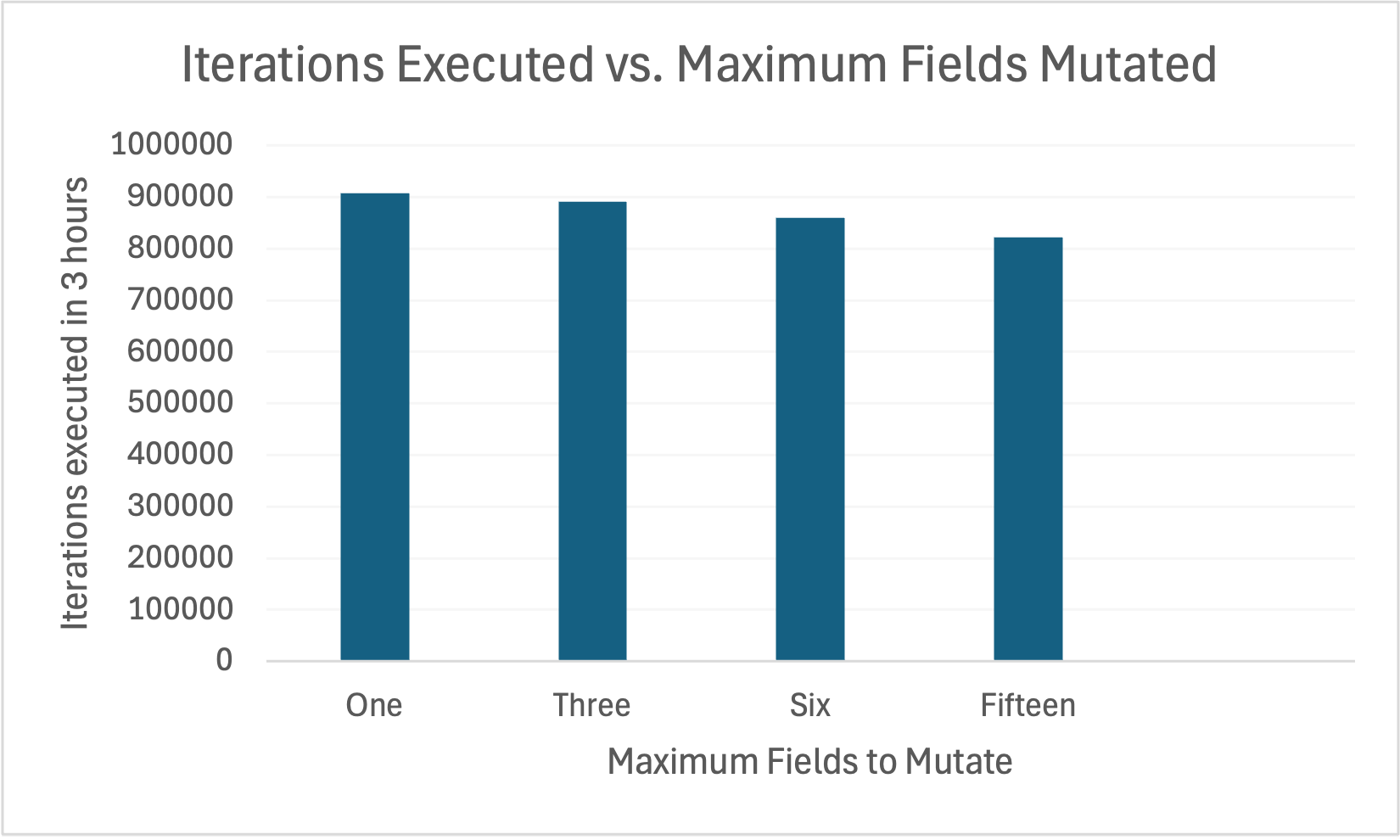
The performance of the Peach fuzzer for different maximum fields to mutatue values
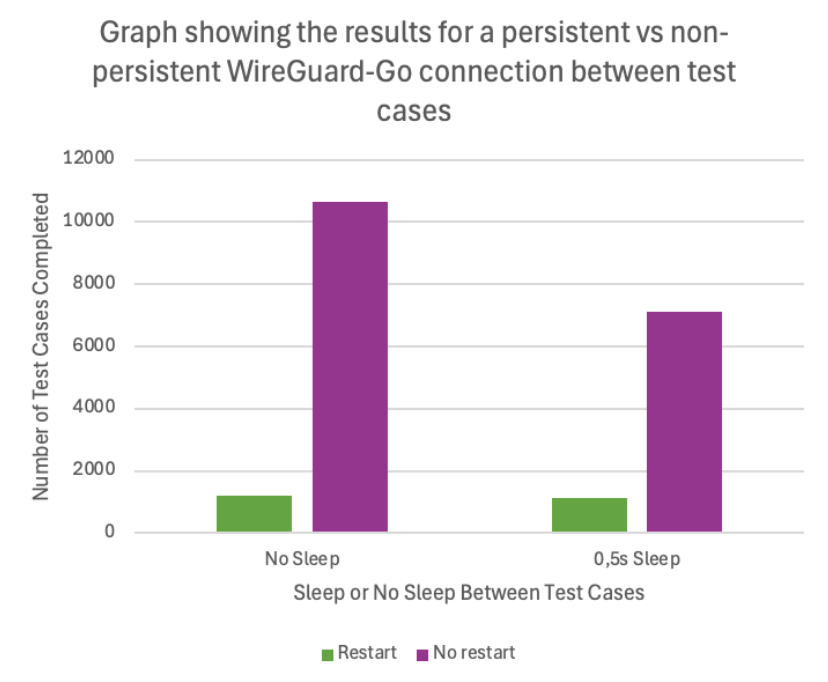
The performance of Boofuzz when target process is run persistently vs restarted
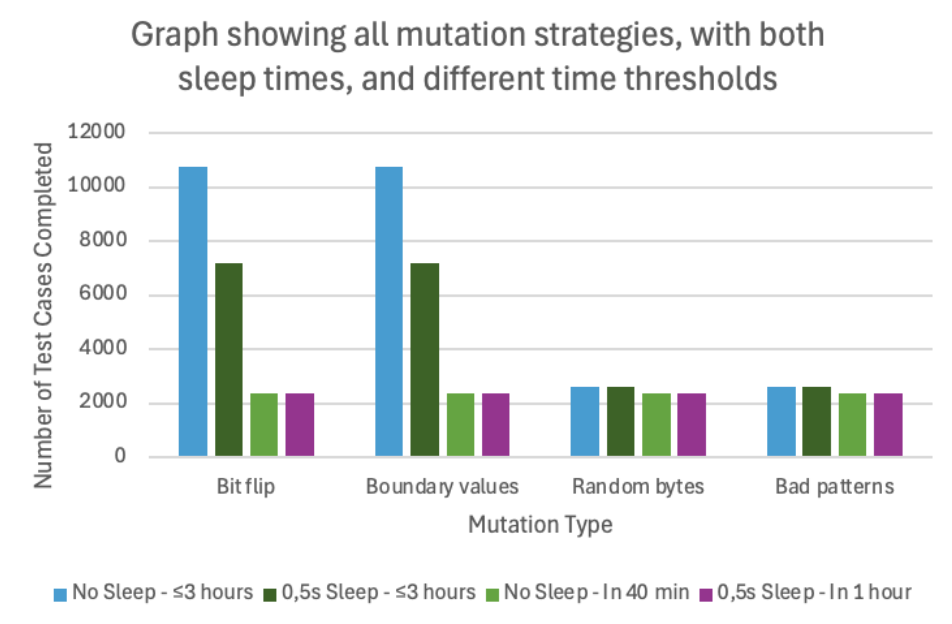
The performance of the Boofuzz for different different mutation strategies
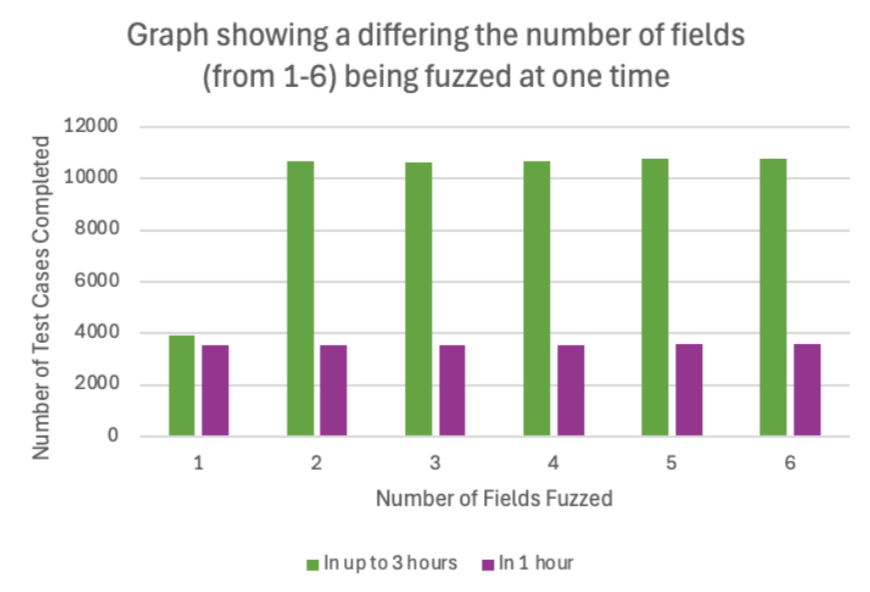
The performance of the Boofuzz for different differented number of fields fuzzed at one time

Title Image